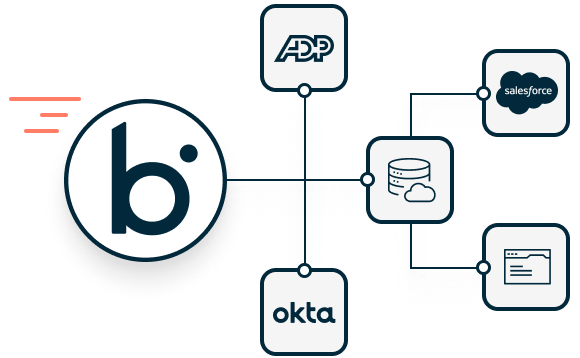
How it Works
Connect applications faster with pre-built integration and the guidance of over 200M machine learning integrations. Spend more time on innovation and less on maintenance with intelligent integration and automation.
Pre-built connectors and recipes
Integrate faster and easier
Select from a large library of pre-built application connectors and integration recipes to jumpstart your integrations.
Intelligent integration and automation
More innovation, less maintenance
Eliminate manual upgrade time, costs, and headaches associated with legacy middleware. Let intelligent integration and automation handle the maintenance to enable your team to focus on innovation.

Intelligent guidance
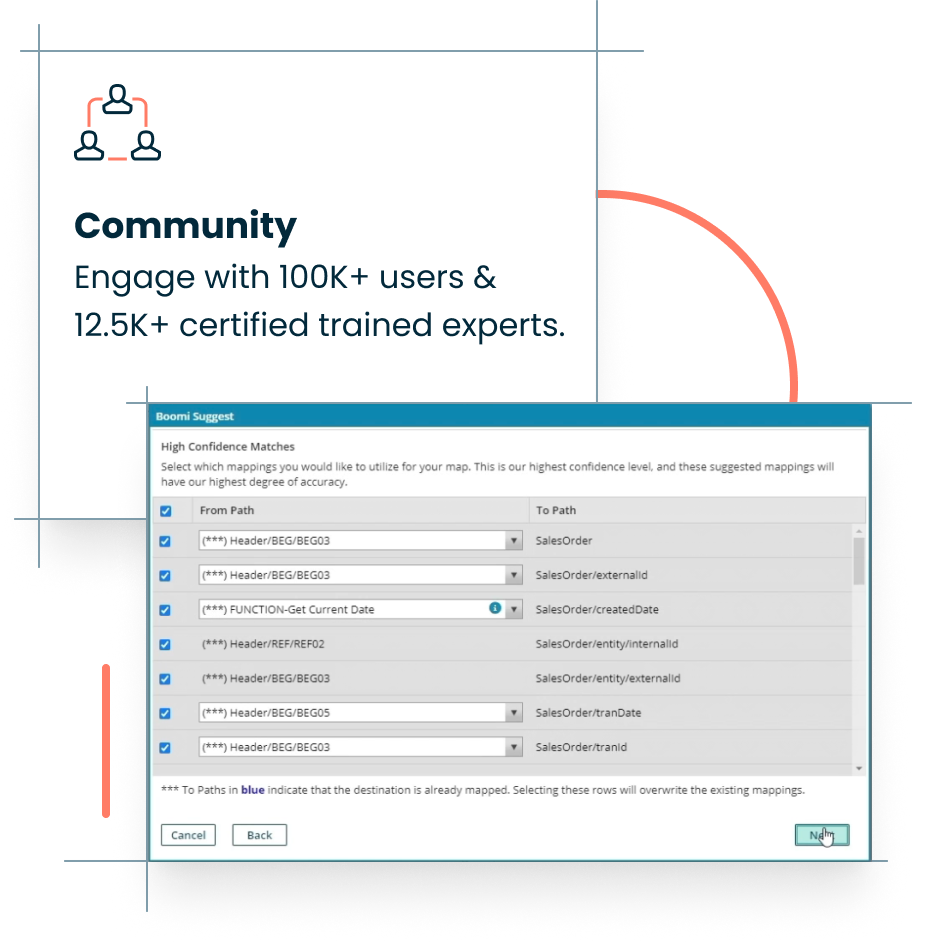
Leverage the Boomi community
Knowing what data to map between applications can be one of the most challenging aspects of integration. Boomi Suggest applies machine learning to over 10 years of crowdsourced intelligence, providing high-quality recommendations to simplify integration.
iPaaS Integration Features
-
Pre-built connectors
Plug into Boomi connectors to eliminate the time consuming task of exchanging data between applications and other data sources.
-
Hybrid deployment
Single instance, multi-tenant architecture ensures your integrations in the cloud, on-premises, and at the edge are never out of synchronization.
-
"Suggest" Integration guidance
Get self-learning with over 200M integrations, crowdsourced for machine learning to simplify mapping of entities between applications.
-
Single platform experience
Easily leverage additional platform services such as EDI and API Management with the same user experience as Boomi Integration.
-
Self-managed
Automatic platform updates deploy synchronized changes to your integration processes to keep your focus on innovation.
-
Regression-tested integrations
Optionally upload test versions of your integrations to Boomi Assure to minimize regressions from software updates.
-
Crowdsourced troubleshooting
Common errors resolved within the UI, based on crowdsourced contributions from the Boomi support team and the user community.
-
99.99% Uptime
Get higher SLAs with Boomi's intelligent integration and automation, enabling your on-premises integrations to synchronize – even if you have a break in your internet connectivity.
Power of the platform
Use your Boomi integration skills to easily add workflow automation, B2B/EDI, API management, data hub, or catalog and preparation.
Extend integration with EDI >
Leverage the Boomi integration skills you already know to seamlessly extend your integrations to your trading partners with Boomi EDI.
API-enable your integrations >
Easily expose your integrations with secure Boomi API Management to for reuse without getting burdened by complex legacy-style API management.
Enrich trusted data >
Create a single source of truth with an easy and flexible secure data management service. Leverage Boomi Data Catalog and Prep to discover and govern your data.
Automate workflows and build applications >
Build applications and automate workflows with the Boomi Flow low-code and cloud-native platform service.











